Home networking and preventing DNS leaks
published on 2024-10-13 by hyperreal
I’m thinking of getting my OPNsense device back up again. At my previous place of residence, I had AT&T internet, and AT&T had all sorts of configurable options in their modem that played well with my OPNsense device. At my current place of residence, I have Xfinity Comcast, and the only option I can configure on their modem that would allow me to use my OPNsense device is “Enable/disable bridge mode”. When I first moved in here, I tried doing that, but for some reason the IPv4 gateway on my OPNsense device wasn’t picking up anything. I believe I had everything configured correctly, the Xfinity modem was in Bridge mode, and the OPNsense router was assigned the public IP address from my Xfinity account. This was four months ago, and it’s very likely I missed something in the configuration, so it can’t hurt to try again. The worst-case scenario is that I reset my Xfinity modem to factory defaults and continue to use that. But it would sure be nice if I could have more control over that portion of my internet.
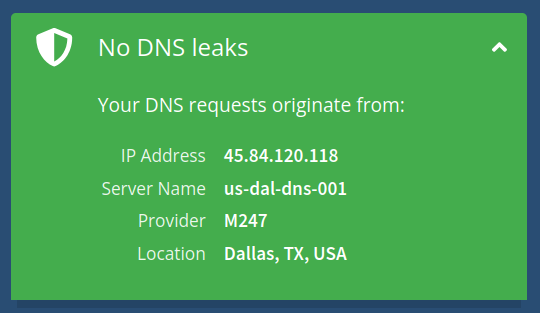
I think I’ve figured out how to prevent my Fedora Linux desktop from leaking DNS to Xfinity. My Linux desktop is part of a Tailscale network that uses Mullvad’s ad-blocking and malware blocking public DNS server, but I still have DNS leaks because my main network interface is using the Xfinity DNS servers from its DHCP connection via the Xfinity modem. Below are the steps I took to prevent DNS leaks to Xfinity.
systemd-networkd
NetworkManager is the default on Fedora 40. I disabled NetworkManager and enabled systemd-networkd with the following configuration:
[Match] Name=eno1 [Network] DHCP=yes DNS=100.100.100.100 DNSSEC=allow-downgrade [DHCPv4] UseDNS=no
In the [DHCPv4] section, UseDNS=no ensures that you’re not using the DNS servers provided by the DHCP connection. In my case, my DHCP connection via my Xfinity modem was setting the DNS to the Xfinity DNS servers. So that is no longer the case now. For good measure, I added my tailnet’s DNS as a static DNS server in the [Network] section.
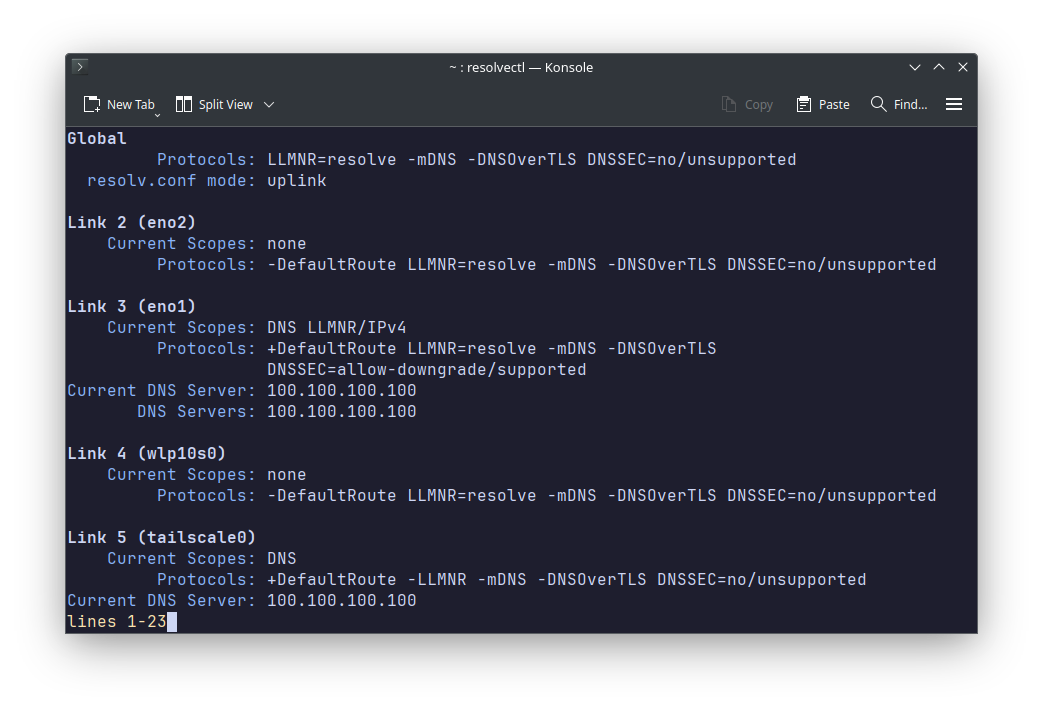
resolvectl status now shows that my primary network interface eno1 uses only the DNS from my Tailscale network, which is 100.100.100.100.
Disable IPv6
Another possible source of DNS leaks is IPv6. On Fedora 40, the way to disable IPv6 is by adding a kernel argument to the GRUB bootloader configuration. This can be done with the following command:
sudo grubby --args=ipv6.disable=1 --update-kernel=ALL
Reboot the system for the change to take effect.
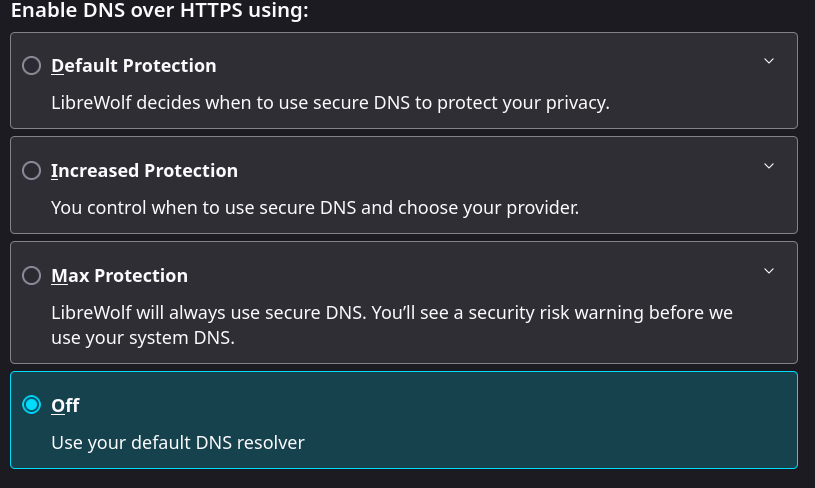
Ensure Firefox or LibreWolf are not using DNS over HTTPS
In most cases Firefox/LibreWolf are configured to use the system DNS resolver by default, but if you have it configured to use one of the “protection” settings for DNS over HTTPS, this could be a source of DNS leaks.
Check for DNS leaks with Mullvad’s connection checker